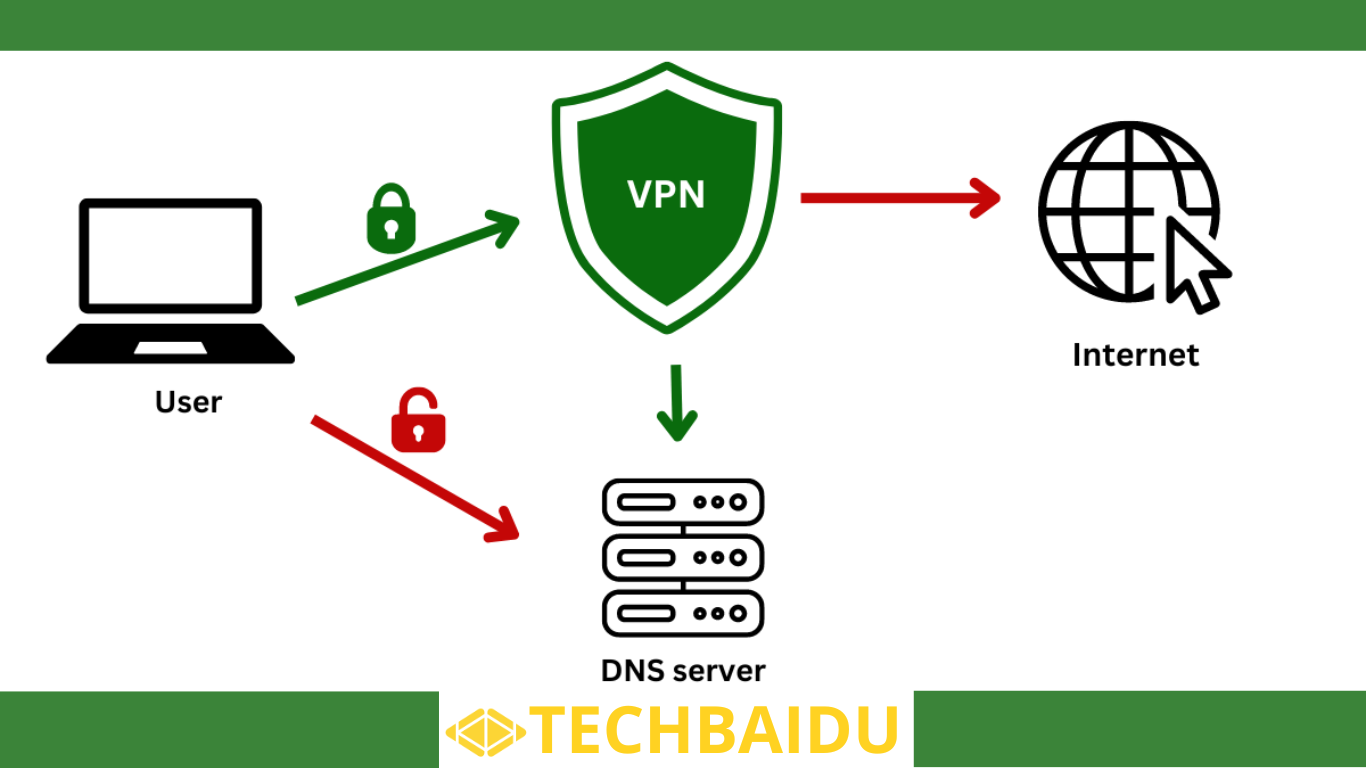
The internet leak, with its open flow of information, presents a paradox: leaks. Confidential data, from corporate secrets to government plans, can be exposed online, wielding immense power. Are leaks inherently good or evil? The answer lies in their complex duality.
On the one hand, leaks can be forces for good. They bring wrongdoing to light, empower marginalized voices, and even trigger reforms. Whistleblowers leaking classified documents have sparked crucial discussions on civil liberties, while corporate leaks have exposed unethical practices, leading to better consumer protection. In these cases, leaks act as vital checks on power, demanding transparency where it’s lacking.
However, this power cuts both ways. Leaks can also have devastating consequences. Personal privacy can be shattered, national security compromised, and individuals targeted. Sensitive information released without context can fuel misinformation and manipulation. Leaks can destabilize international relations and erode trust in institutions. Therefore, judging them as purely good or evil is an oversimplification. They are a powerful tool that can be used for both positive and negative ends. Understanding the nuances of each case and fostering responsible leak practices are crucial for navigating this complex terrain and maximizing the internet leak potential for good while mitigating the risks.
Shining a Light on Darkness internet leak
Leaks have played a crucial role in揭露不公正和滥用权力. From the Panama Papers exposing financial corruption to the Snowden leaks揭露政府大规模监控,这些信息披露引发了全球讨论,并导致了政策改革和问责制. Without such leaks, powerful entities could operate with impunity, and injustices could go unnoticed. In this sense, leaks serve as a vital check on power, empowering citizens to hold institutions accountable.
The Price of Transparency
However, leaks also come with significant downsides. Sensitive information, even when exposing wrongdoing, can have unintended consequences. National security secrets leaked by Edward Snowden, while raising concerns about government surveillance, also put intelligence operations at internet leak and potentially endangered lives. Leaks can also have a chilling effect on whistleblowing, as individuals fear the personal and professional repercussions of their actions.
Beyond Black and White
The impact of a leak ultimately depends on the nature of the information exposed, the methods used to obtain it, and the motivations of the leak. Leaks driven by personal vendettas or financial gain can be harmful, while those motivated by public interest and a desire for justice can be catalysts for positive change.
The Erosion of Trust and Privacy: Leaks as Weapons of Destruction
However, internet leaks can also be devastating, eroding trust and causing widespread harm. Leaks of sensitive medical data can compromise patients’ privacy and expose them to discrimination or even physical harm. Corporate leaks can damage business reputations and cost jobs. Moreover, malicious actors can weaponize leaks to spread misinformation, manipulate public opinion, and destabilize governments. Leaks used for personal gain, revenge, or political agendas can have far-reaching negative consequences, highlighting the dark side of unchecked information exposure.
Shining a Light on Injustice: Leaks as Catalysts for Change
Internet leaks have played a crucial role in exposing wrongdoing, corruption, and human rights abuses. From the Panama Papers uncovering financial misconduct to the Snowden leaks revealing mass surveillance programs, these revelations have sparked public outrage and forced institutions to answer for their actions. These leaks can empower marginalized communities, hold powerful individuals accountable, and trigger much-needed reforms. For example, the WikiLeaks release of US military documents from the Iraq War led to increased scrutiny of military actions and public pressure for accountability.
The Perilous Path: Unforeseen Consequences and Ethical Dilemmas
However, internet leaks are not without their downsides. They can have unintended consequences, jeopardizing national security, putting individuals at risk, and eroding trust in institutions. Classified information, even if used to expose wrongdoing, can be weaponized by malicious actors. Additionally, the motives and methods behind leaks often need to be more credible. Are leakers whistleblowers acting in the public interest, or are they driven by personal agendas or vendettas? Leaks can also have a chilling effect on free speech, as individuals may self-censor for fear of repercussions.
Navigating the Gray Area
Therefore, judging leaks solely as good or evil is an oversimplification. We need a nuanced approach, considering the context, intent, and potential consequences of each disclosure. This requires健全的新闻业和媒体素养,以确保准确和负责任地报道敏感信息. Additionally, robust legal frameworks are needed to protect whistleblowers while safeguarding national security and individual privacy.
Ultimately, the internet leak dilemma presents a complex challenge. While leaks can be powerful tools for exposing wrongdoing and fostering accountability, they can also have harmful consequences. Our responsibility is to navigate this gray area with critical thinking, ethical considerations, and a commitment to using information responsibly for the greater good.
Navigating the Moral Maze: Striking a Balance
Whether leaks are good or evil depends on the context, intent, and consequences. While internet leak can be powerful tools for exposing wrongdoing and driving positive change, they can also be instruments of harm and manipulation. Finding the right balance requires a nuanced approach. Robust whistleblower protection mechanisms are crucial to encouraging responsible disclosure of wrongdoing. Simultaneously, strong safeguards are needed to protect individual privacy and prevent harmful leaks of sensitive data. Ultimately, navigating this ethical minefield requires a collective effort from individuals, institutions, and policymakers to ensure that leaks are used responsibly and ethically, maximizing their potential for good while minimizing their potential for harm.
It is important to remember that an internet leak is a tool and like any tool, it can be used for good or evil. It is up to us, the users, to decide how we will leverage the power of leaks and ensure that they contribute to a more just and equitable world.
Final Thoughts
judging internet leak as inherently good or evil paints an incomplete picture. They represent a double-edged sword, capable of both positive change and significant harm. On one hand, their ability to expose wrongdoing, empower marginalized voices, and trigger reforms makes them invaluable tools for accountability and justice. Whistleblowers leveraging leaks have sparked landmark conversations about civil liberties and corporate responsibility.
However, we must acknowledge the potential for devastating consequences. Internet leak information can violate privacy, compromise security, and fuel misinformation. Leaks can destabilize international relations and erode public trust in institutions. Therefore, a nuanced approach is essential. Understanding the motivations behind each internet leak, and its potential ramifications, and fostering responsible leak practices are crucial for navigating this complex terrain. Only then can we maximize the internet’s potential for good while mitigating the risks associated with this powerful tool.
Ultimately, the impact of an internet leak hinges on the context and its responsible handling. By fostering open dialogue, critical thinking, and responsible leak practices, we can harness the power of leaks for positive change while minimizing the potential for harm. This approach is crucial for navigating the complex and ever-evolving digital landscape, ensuring that the internet remains a force for good.
FAQs
1. What constitutes an “internet leak”?
An internet leak occurs when confidential or sensitive information is unintentionally or unauthorizedly released online. This can happen through various means, such as hacking, insider leaks, misconfigured databases, or accidental data dumps.
2. Are all internet leak bad?
Not necessarily. Internet leak can expose important truths, prompting public discourse and positive change. For example, leaks like the Panama Papers revealed widespread financial corruption, leading to investigations and reforms.
3. What are the potential downsides of internet leak?
Internet leak can have serious consequences, even if well-intentioned. They can compromise national security, endanger individuals, and erode trust in institutions. Sensitive information, even when exposing wrongdoing, can be misused by malicious actors.
4. Who decides if a leak is good or bad?
There’s no easy answer. Evaluating the impact of an internet leak requires considering the type of information exposed, the leak’s intent, and its potential consequences. This often involves complex ethical and legal considerations.
5. How can we ensure responsible reporting on leaks?
Journalistic integrity and media literacy are crucial. Reputable media outlets verify information, consider context, and prioritize responsible reporting to minimize harm while informing the public.
6. What legal frameworks exist for leaks and whistleblowing?
Laws regarding leaks and whistleblowing vary across countries. Some offer protections for individuals exposing wrongdoing, while others impose strict penalties. Striking a balance between transparency and accountability remains a complex legal challenge.
7. What can I do to stay informed about leaks?
Follow reputable news sources that critically analyze leaks and provide context. Be cautious about unverified information circulating online. Utilize resources like “Have I Been Pwned” to check if your data has been exposed to known breaches.
8. How can I protect myself from the potential harm of leaks?
Stay vigilant about online security practices, use strong passwords, and be mindful of the information you share online. Consider data breach monitoring services and be prepared to respond if your information is compromised.
1st: https://techbaidu.com/category/course/artificial-intelligence/
2nd: https://techbaidu.com/mobile-app-obfuscation-a-guide-to-protecting-your-code/
3rd: https://techbaidu.com/disclaimer/
4th: https://techbaidu.com/trump-nft-watermark-a-saga-of-controversy-and-copyright/
5th: https://techbaidu.com/creating-custom-memoji-android-a-step-by-step-guide/